Wireless penetration testing
These tests will also include elements of Social Engineering for example redirecting users to a fake webpage in an attempt to capture sensitive log in information and other data. We start off with a look at fundamental analysis techniques for evaluating WiFi networks, including the identification and analysis of rogue devices, and finish with a dive into remote penetration testing techniques using compromised Windows 10 and macOS devices to pivot. Testing and Exploitation Utilising the information and standards identified in the analysis phase, various aspects of the wireless security controls are tested to find potential vulnerabilities. There are a number of goals that need to be achieved: We use Perl for day to day on-the-fly scripting during all types of penetration testing, but we also use it to generate most of the reports used internally during a wireless penetration test. Our clients reach to us when wireless access point challenges vague and they are not confident that clients have the internal capability to meet their wireless security controls in a cost effective manner for their organization.


Kali Linux Wireless Penetration Testing Beginner's Guide, 3rd Edition - PDF eBook Free Download




Wireless Penetration Testing Checklist – A Detailed Cheat Sheet
Set up a giveaway. So you will not enjoy this book unless you really aim to understand what you're doing, which is not what most new security folks care about. You have successfully subscribed to our newsletter. Path to access fern cracker inside backtrack directory: Customers who bought this item also bought.


Customers who bought this item also bought
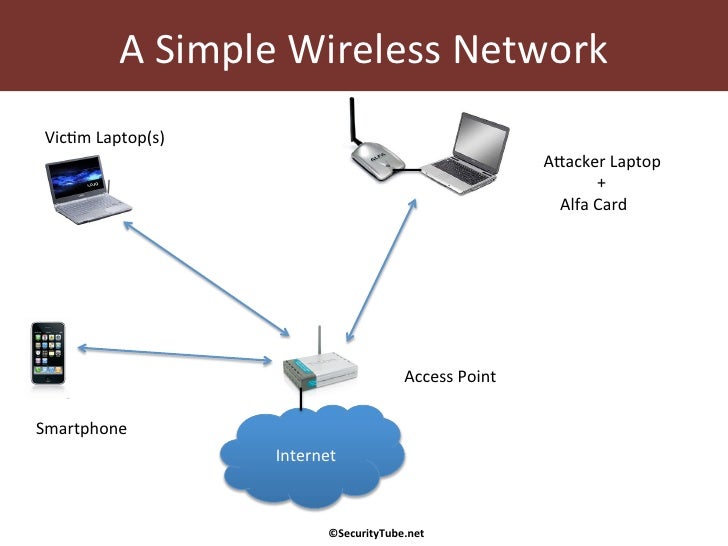
Previously, Cameron was a member of the RAF. The Passphrase provides security encryption for your wireless network. Monitor mode is a special mode that allows PC to listen to every wireless packet. ZigBee is defined by




These are used to track user interaction and detect potential problems. The MAC address of the Access Point as Basic Service Set Identifier- its Ethernet address PWR Signal strength. For example, as well as the ESSID we can also see the BSSID. Wireless Pen Test Tools. Plug wireless card Alfa Card in virtual machine. In the following screenshot we can see more information about the network.

338
32
















Seeing a married man who likes to shoot his load on my face and glaze up my eyes. Says it really makes his ejaculation feel better.
Can i suck your pussy
turn off the music I want to hear her
Sex ohne Penetration !
super f?st?k l? lokum
super sexsi
we love swing clubs
[email protected]
My body, my choice! В
Perfekt shaped girl, perfekt tinny tits. Last week I sucked a pair like this...