Penetration testing of networks
But analysts said the fanfare The results of a penetration test may vary depending on its scope and time frame as well as the abilities of individual testers. Attempting to exploit vulnerabilities like system configuration flaws or weak passwords and break into an organization's information systems Reporting: Join the DZone community and get the full member experience. Some of the reporting features include: For more information on how you can use vulnerability assessment as your own penetration testing tool, please call, email or use the form on this page. These tools should have a continuous development cycle and updates of their knowledge base.


Network Security and Penetration Testing | Core Security




Network Penetration Testing
Email Us Email Us??? The study touched off more than a decade of quiet activity by elite groups of computer scientists working for the Government who tried to break into sensitive computers. By using this site, you agree to the Terms of Use and Privacy Policy. The process typically identifies the target systems and a particular goal—then reviews available information and undertakes various means to attain the goal. Customers who viewed this item also viewed.


Customers who bought this item also bought
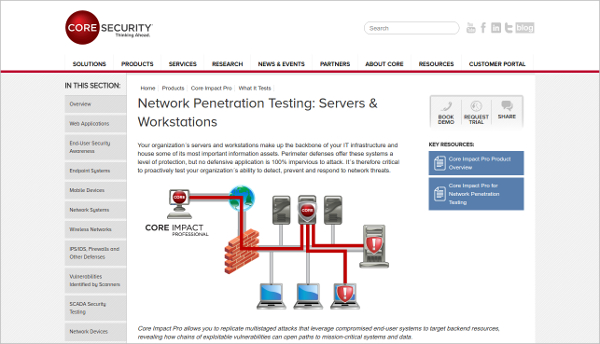
The detailed reports that pen-tests generate can help organizations avoid significant fines for non-compliance and allow them to illustrate ongoing due diligence in to assessors by maintaining required security controls to auditors. We deliver comprehensive security intelligence that lowers risk, prioritizes solutions, and minimizes business disruptions. Yost of the Charles Babbage Institute, in his own work on the history of computer security, also acknowledges that both the RAND Corporation and the SDC had "engaged in some of the first so-called 'penetration studies' to try to infiltrate time-sharing systems in order to test their vulnerability. Presenting companies with a detailed vulnerability report and recommendations for improvement, network penetration testing enables IT departments to validate existing security controls and meet security compliance requirements while allowing managers to better prioritize investment for remediation efforts.




So, automation should be followed by manual checking. Dealing with attacks inside networks Royal Holloway This is the latest and by far one of the best penetration test tools for application testing from the developers of Metasploit. Two important stages are left: This section covers best practices followed by pentesters while conducting network penetration testing. A combo of the two methods boosts the effectiveness of the process considerably.

916
35

















sweet, mmm
You must be rich and she's a gold digger. Why she'd be with you is illogical.
Ummmm.......start with a kissing boobies relationship
The blond thing, well.we'll visit that next time.
love to fuck her, she's so dirty and if she were my gf i'd enjoy her having other men when ever she wants, also be gr8 sticking my cock in her after she's had several guys spunking their balls off deep inside her, check out my gf pics and vids, she's a real slag and had loads of men
Lubes fucking expensive though
nice
uma bosta me desculpa falto criatividade para expor ..!!!!